Over fifteen years ago, the launch of Amazon Web Services (AWS) ushered in a new era of Information Technology (IT) services where businesses transitioned their systems from traditional environments of physical servers hosting business applications to cloud-based environments using virtualized, containerized, and decentralized services.
Navigating the information security landscape can be daunting, particularly when organizational enterprise systems reside across unclear boundaries. An additional layer of complexity exists with the Cloud Security Shared Responsibility Model, which outlines the security responsibilities of cloud service providers (CSPs) and customers based on cloud service type.
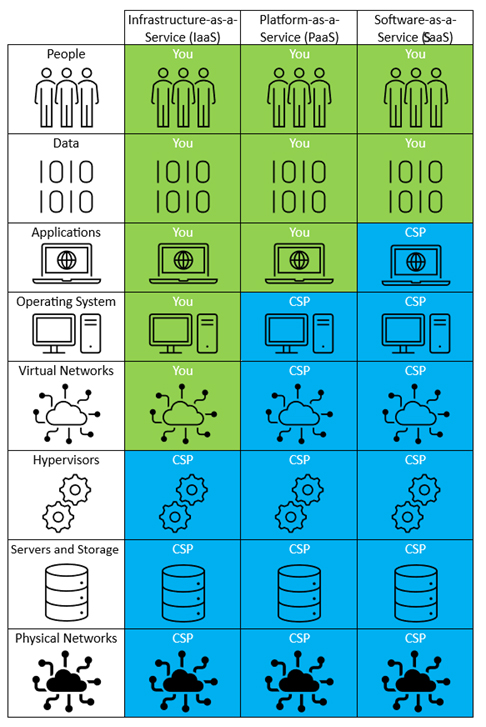
Cloud Security Shared Responsibility Model
Referring to the Cloud Security Shared Responsibility Model image, the customer is responsible for securing and protecting the green gap areas not covered by CSPs. Standard secure configuration guidance, such as the Center for Internet Security (CIS) benchmarks, identifies areas of configuration weakness often integrated as policy checks in Cloud Security Posture Management (CSPM) solutions.
Prowler is an open-source security tool that can help proactively harden cloud services not managed by the CSP, validate compliance against third-party audit findings, and support audits and assessments of cloud environments. Using AWS as an example, Prowler uses the AWS command-line interface (CLI) and can validate policy checks against the CIS AWS Foundations Benchmark and other compliance standards, such as AWS Best Practices, Federal Financial Institutions Examination Council (FFIEC), Federal Risk and Authorization Management Program (FedRAMP), General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), International Organization for Standardization (ISO) 27001, MITRE Adversarial Tactics, Techniques, and Common Knowledge (MITRE ATT&CK), National Institute of Standards and Technology (NIST) 800, NIST Cybersecurity Framework (CSF), Payment Card Industry Data Security Standard (PCI-DSS), System and Organization Controls (SOC) 2, and custom security frameworks. Results from a Prowler assessment can be generated as standard output (e.g., CSV, HTML, JSON, etc.) or
integrated with the AWS CSPM service Security Hub for import and central consolidation of reported findings to support remediation activities.
The compliance frameworks utilized offer over 240 security configuration checks related to several cloud services, such as Amazon Elastic Compute Cloud (EC2), Simple Storage Service (S3), Identity and Access Management (IAM), Elastic Block Store (EBS), CloudTrail, RedShift, ElastiCache, API Gateway, and CloudFront, to name a few.
An example of standard Prowler usage could be from a locally deployed Amazon Elastic Container Service (Amazon ECS EC2) instance scanning checks across the Virtual Private Cloud (VPC). Validation checks selected and raised as potential issues during the scan can collate as output for inclusion into the AWS Security Hub for later remediation. Some examples of findings may include deleting expired, non-rotated IAM access keys, enabling server-side encryption for S3 buckets, or deleting unencrypted EBS volumes.
DevOps usage of infrastructure as code (IaC) for automation of management, provisioning, and configuration of cloud infrastructure is a convenient way to deploy resources rapidly or at scale. However, increased automation with IaC may lend itself to misconfiguration, which may also automate configuration flaws. Prowler can support validation efforts in identifying configuration anomalies from IaC deployments, particularly across multiple VPCs or AWS Organization accounts.
Prowler locally or remotely assesses AWS cloud environments:
1. Prerequisites:
•
AWS CLI installed and configured on the machine.
• An AWS account with appropriate permissions.
1. Associate credentials with the user/role performing necessary checks.
2. Assign adequate permission to the user/role performing checks, and add the following AWS-managed policies to the user/role:
• arn:aws:iam::aws:policy/SecurityAudit
• arn:aws:iam::aws:policy/job-function/ViewOnlyAccess
• Python 3.6 or higher installed on the machine.
• Git installed on the machine.
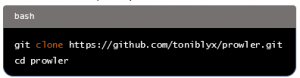
2. Clone the Prowler repository:
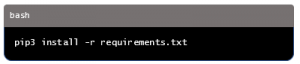
3. Install required Python packages:
4. Configure AWS CLI with appropriate credentials:
Enter your AWS access key, secret key, default region, and output format when prompted.
To run Prowler, specify the CSP (e.g., AWS, GCP, or Azure):
CIS checks are run by default without any additional arguments:
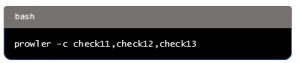
To run specific checks, use the -c flag followed by the check numbers:
To run checks for specific groups, use the -g flag followed by the group name:
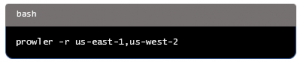
To run checks for specific AWS regions, use the -r flag followed by the region name:
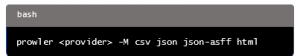
Prowler natively supports various output formats, such as CSV, JSON, JSON-OCSF, HTML, and JSON-ASFF (specific to AWS Security Hub), using the -M flag.
7. Analyze the output:
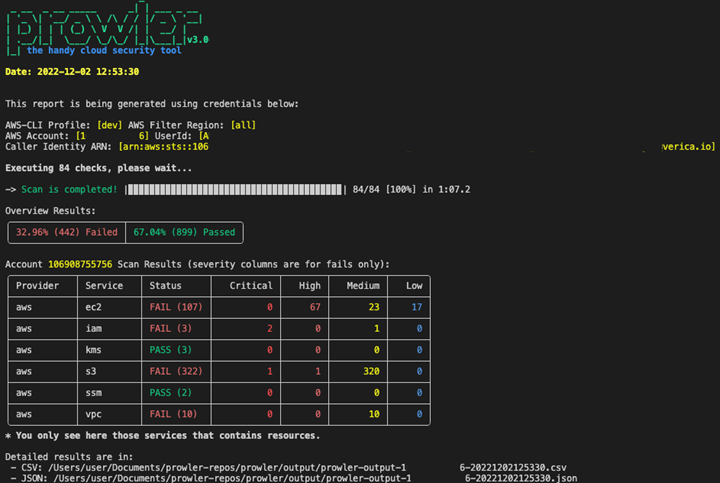
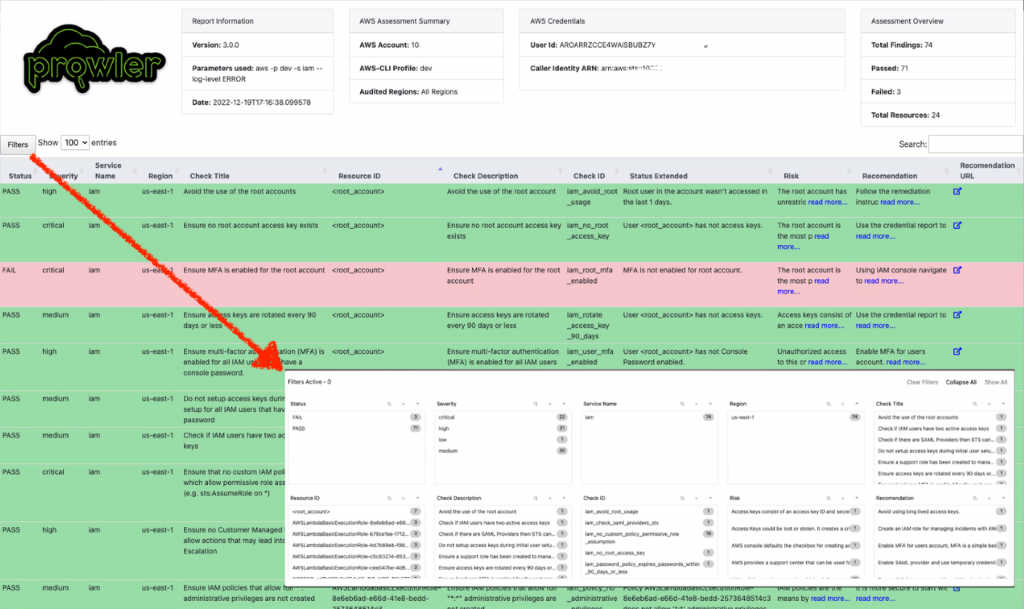
Report output is, by default, located in the output directory as a file with the following nomenclature prowler-output-ACCOUNT_NUM-OUTPUT DATE.format. However, you can generate custom location and filename using the -F flag. Here is a sample snapshot of HTML output:
Prowler provides the assessment results in a clear, human-readable format. It includes the test number, status (PASS, FAIL, or WARNING), description of the test, and any relevant information or resources associated with the check.
8. Remediate identified issues:
Review the assessment results and prioritize remediation actions based on the risk and impact of the identified issues. Use the detailed information provided in the Prowler output to understand and address each case accordingly.
Nexum Can Help
If you’re looking to assess your cloud posture, Prowler is a great way to start; if you’re looking to take the next step, Nexum can not only help you evaluate your results, but also take a more holistic look at your cloud security needs. From assisting with selection and implementation of a full CSPM tool to performing cloud security assessments and penetration testing, Nexum has the in-house resources to help you protect your cloud environments.